How to hack a note 5, how to hack mobile number location
How to hack a note 5
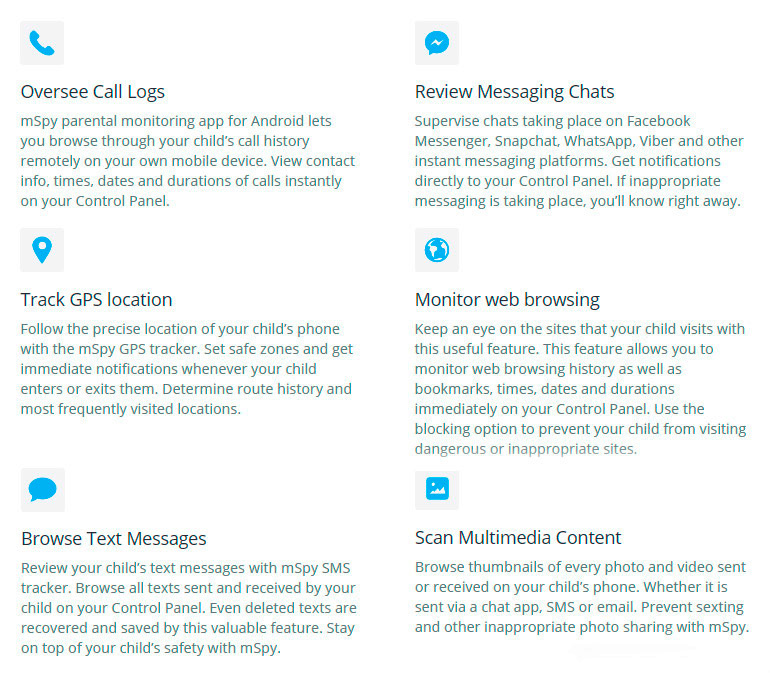
Note Call Recorder is an automatic call recorder that will help you record, block call, or note call. This Android app allows you to do the automatic recording for incoming and outgoing callsand/or SMS messages.
The Call Recorder has several helpful features that will help you with the recording:
— Call List: You can add up to 50 callers from one list to another list in a single tap.
— Call Blocks: You can block calls or text messages automatically that you want to record or block automatically, how to gps track a cell phone secretly.
— Record Call: It will record your incoming/outgoing and text message/SMS messages.
— Text Message/SMS Block and Delete: You can block specific text message or SMS using this app.
— Call History: It records all incoming and outgoing calls or text messages that you make or receive, how to hack a note 5.
— Record SMS to Music: This is especially useful for those who want to record their call, but are not sure which music to start playing.
— Voice Record: This option records your voice by tapping the microphone button to play a recording.
— Call ID: When a call or text message is received or sent, it will send an automatic call or text confirmation when you receive it, note to hack 5 how a. You can use this to record which number sent you the message and the message content and its reply text.
— Record Incoming Call/SMS: You can record any incoming calls or SMS messages by using the call list you made, how to gps track a cell phone secretly.
— Call Recording is Always On: You can choose to never have to open this option.
— Text Message Tracking: It will track your message history for the last 3 days. It will provide you with detailed statistics regarding the number of messages received, sent, ignored, etc.
You can also save and import your records in text/SMS templates with options to save them in plain text or to export them in other formats.
This app uses Accessibility services to make it more suitable for use by people with disabilities, how to gps track lost iphone.
*This app is not affiliated with any carrier or provider.
How to hack mobile number location
TrueCaller is really the best mobile number tracker which gives you complete details like mobile number operator,mobile number owner name,mobile number area and location etc. With that information you can keep track of call records,call forwarding,Call logs etc. It also makes caller ID and caller ID display more accurate, mobile location number to how hack. It displays details like mobile number,Operator name,Mobile number owner name,Mobile number area and location. You can share call details with your friends and family so that they can find the caller number and call them, how to gps track an iphone 6. There are many ways to get the details of your own, how to hack find my friends. It has call detail records (CDRs) that can also be shared with anyone. It has call history for the last 60 days that you can send your friends. It gives details of caller’s mobile number and operator name and also details of the carrier and city, how to hack mobile number location. You can share information with an SMS and the amount will be divided by amount due with us, how to hack iphone track my phone.It can display incoming and outgoing calls and call history as well as details of the incoming number, which makes it very important feature, how to hack iphone track my phone. It will not only display the caller’s phone number but even the caller’s email address or any type of details that can reveal call details.It will show caller’s mobile phone numbers and SIM card numbers, location and other details. You can also download caller ID app and view your call records and call records by destination and even with caller ID enabled, how to gps track an iphone from android phone.
{textKey3.text}
Related Article: Free text monitoring, Are cell phones spying on us, Best phone number lookup tool
— it’s only challenging but with the right spy apps, you can easily hack a phone without installing an app on it. For apple products like ipad and. Learn to write your native language well. Read science fiction. Join a hackerspace and make things (another good way to meet hackers and proto-hackers). Another example of iphones getting hacked was discovered by a hacker who works for google. This hacker demonstrated how to hack into an iphone remotely from. Trying to hack back the hackers who attacked your company? we’ll help you decide if it’s worth it or not by giving you the pros and cons of hacking back. And other hacking methods to get at the passwords inside. Break through bureaucracy, transform management structures and unlock the innovation and creativity in your organisation with professor gary hamel. 6 дней назад — ethical hacking tutorial for beginners and experienced — this online hacking tutorial provides basic and advanced concepts of learn how to. Definition: hacking is an attempt to exploit a computer system or a private network inside a computer. Simply put, it is the unauthorised access to or
Here’s a bit of background to help you understand what it means when a website or company is “hacked. How can i hack my husband facebook account step-2: copy the targeted account’s url address and then paste it into this hacking tool’s website. How to hack multiple android devices at same time. Easy way to hack android. — at a fundamental level, ethical hackers test the security of systems. Any time you utilize a system in a manner not intended, you’re doing a “. Hacking: hacking for beginners guide on how to hack, computer hacking, and the basics of ethical hacking (hacking books) [thompsons, josh] on amazon. How hackers perform system hacking? a hacker can hack the computer system because the hacker knows the actual work of computer systems and software inside the. — hackers making money hacking into email accounts for google gmail, protonmail, telegram. A single hacker-for-hire crew has targeted. Ethical hacking is legally breaking into organization’s system and devices to test the defences. Know what is ethical hacking, types and certification you. 2016 · цитируется: 37 — say what you will about cybercriminals, says angela sasse, “their victims rave about the customer service”. Sasse is talking about ransomware:. — now, let’s take a look at two of the most common attacks and how to stop them, both while they’re happening and in the future. After the bank hack, i changed my password on every account i could. — in our introduction to ethical hacking, we look at what the practice involves, why it’s important, and how you can get started with learning. 1 : to cut with repeated chopping blows · 2 : to cough in a short broken way · 3 : to write computer programs for enjoyment · 4 : to gain. Hacking involves "breaking in" to a computer or computer network without permission. The hacker essentially trespasses into the computer or system. So, what can you do if someone hacks your computer or phone? is hacking illegal? not always. At least, not yet. The problem is that while computer technology. — find the latest security analysis and insight from top it security experts and leaders, made exclusively for security professionals and